How to identify a remote access scam
How to identify a remote access scam

What's coming up?
In this activity, you’ll learn how a remote access scam works, step by step via a scenario. You’ll meet Costa, who receives a call from what he thinks is Microsoft, but is actually a scammer. You’ll see how the scammer uses Costa’s limited technical knowledge to convince him to purchase unnecessary software.
Start activityCosta receives a call from a scammer
One day at home, Costa gets a mobile phone call from someone claiming to be from the Microsoft Windows technical department. The scammer tells Costa that Microsoft has detected some serious problems with his computer.
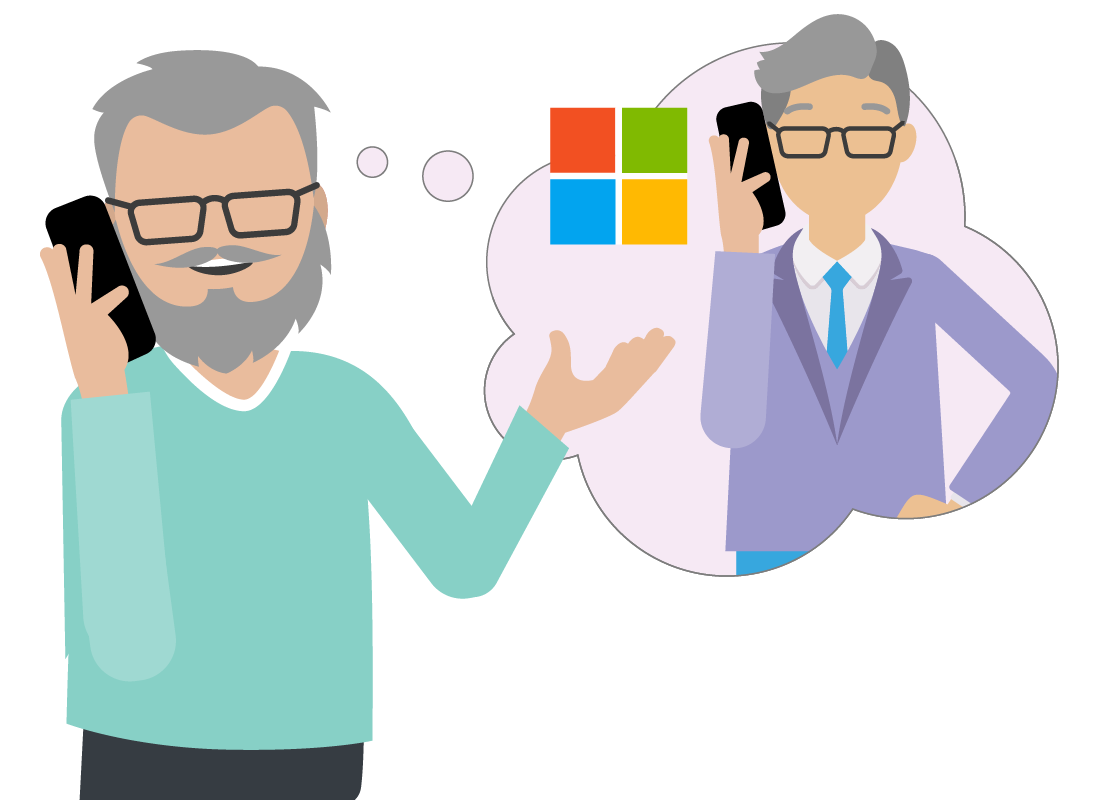

The scammer asks Costa to check his computer
The scammer guides Costa thought some simple steps to bring up a screen on his Windows computer, which shows a list of errors and warnings.
In fact, this screen is a normal part of his computer’s operation, and is just a log of the computer’s internal workings. The errors are real but also normal and the computer has already fixed these itself. Due to Costa’s limited technical understanding, this log causes confusion.

eSafety tip
Using a normal Windows screen to show errors is just one of the tricks that remote access scammers can use. If you are unable or refuse to open this screen, the scammer will move on to a different technique. For example, they may claim a new virus has just come out which no antivirus software (except theirs) can detect and remove.
Costa sees his computer get worse
Costa is concerned by the apparent errors, so he is keen to follow the scammer’s instructions to fix his computer. This gives the scammer even more access, and to Costa’s horror, even more things seem to go wrong as he watches!
The scammer pretends to be very concerned about the state of Costa’s computer.

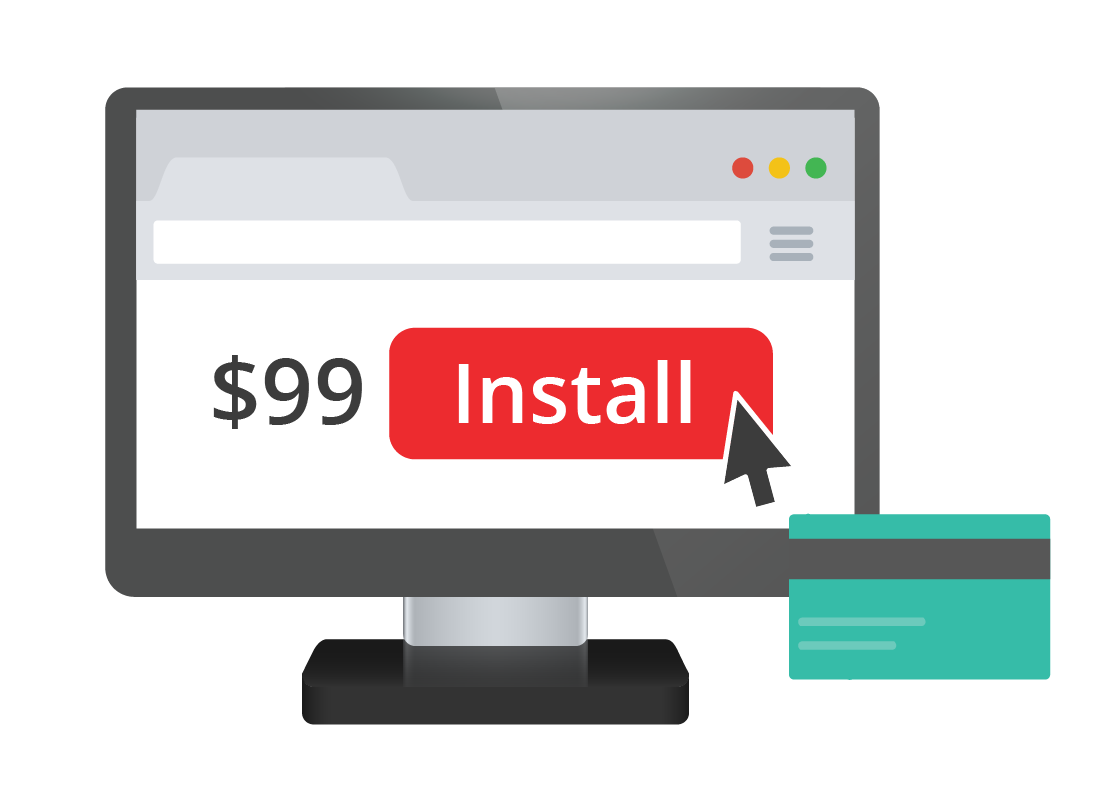
Costa purchases unnecessary software
The scammer has convinced Costa that his computer is in bad shape, and Costa agrees to purchase $99 software to fix the problems. He gives the scammer his credit card details.
The scammer then offers to set up the software on Costa’s computer remotely for him, and Costa agrees.
The computer is infected with spyware
Costa’s computer is now infected with software that shows him constant advertising, tracks his keyboard inputs, and sends his credit card and password details to scammers.


Costa gets suspicious
After a couple of days, Costa starts to get suspicious because his computer has been running much more slowly since installing the scammer’s software.
He updates his antivirus suite, which then detects all the malicious software on his computer and removes it.
Costa realises he has been scammed
Following the antivirus scan, Costa realises he has been scammed. He knows there’s no way to recover the $99 he paid to the scammer, but he changes his passwords to be safe. He also contacts the ACCC’s Scamwatch page at https://www.scamwatch.gov.au/report-a-scam to report the scam.

Well done!
This is the end of the How to identify a remote access scam activity. You’ve learned what a remote access scam can look like, by following along with Costa’s unfortunate experience.
Up next, find out how to avoid being tricked by these scams in the Protecting yourself from remote access scams activity.
